✨ Health insurance, now in PayFit - learn more
💷 All the rates & thresholds you need to know for 25/26...right here
✨ The Payroll Journey: Start, Scale & Succeed Globally - learn more
✨ Health insurance, now in PayFit - learn more
💷 All the rates & thresholds you need to know for 25/26...right here
✨ The Payroll Journey: Start, Scale & Succeed Globally - learn more
At PayFit, we believe it is our duty to keep your data secure. PayFit is ISO 27001 certified by an independent auditor.

Discover how PayFit ensures the security and privacy of your data. Visit our Trust Center to learn more about our robust security measures, compliance standards, and commitment to protecting your information.
Security
PayFit is committed to keeping your data safe and out of the hands of those without authorisation.
Confidentiality
We use several different methods to ensure that your account remains secure at all times. Your data is also encrypted in our database.
Integrity
We strictly control who has access to your data, both online and internally. This is done to ensure that your documents are protected against any unauthorised alterations. We also back them up every hour.
Availability
Real-time data replication to three data-centres in France. We also use automatic failover in the unlikely event that we experience any technical difficulties.
As a certified ISO 27001 company, we are fully committed to securing and protecting your data. We also regularly review our processes to ensure that best practices are put in place.
We are interested in any research on our systems and value any documented discovery. For that purpose, we run a private bug bounty programme on HackerOne so that we can identify and mitigate security threats.
Data storage and backups situated in France.Encryption of all stored data in transit and at rest, including any backup copies.
Data anonymisation or non-transmission to sub-processors.
Mandatory user authentication by email and password (controlled by a strict policy) with the option of two-factor authentication (2FA) via SMS token authentication.Internally, data access, for authorised staff members, is only allowed through a VPN protected by 2FA authentication.
Data transmission through TLS/SSL only with HSTS and perfect forward secrecy fully enabled. PayFit is graded as an "A" rating on SSL Labs' tests.
Access to customer data restricted to identified teams, with a proportional and justified reason to do so. Systematic log of such access.
Centralised management with global inventory, monitoring and alerting capabilities.
Globally enforced and managed device security policy (auto-lock, password complexity and rotation, real-time protection against malware, firewall, disk encryption, restriction on software installation, auto-updates, remote lock and erase capabilities).
Global policy on authorised tools to handle assets by information type and classification frame.
Source code access is strictly controlled, with systematic peer review on new code merging.Centralised rights management on all Software-as-a-Service.
Mandatory global procurement policy prior to any supplier employment, with systematic security, legal and financial authorisation.
Background check on all candidates.
Requirement for all employees to sign a confidentiality agreement and to follow the internal digital policy.
Enforcement of device security policies globally through a centralised management tool with monitoring and remediation capabilities.
Regular security training for all employees and a quarterly review of internal security policies. In order to separate developing roles from consulting and validating roles, we use a RACI matrix framework for the development and management of all tasks.
Physical access to PayFit facilities is protected by personal identification badges.
Offices are monitored 24/7 by CCTV and alarm systems.
Physical access control logs maintained for 45 days.
Mandatory supervision of visitors and external staff by a PayFit staff member.
Frequent tests and updates of our payroll software by the best experts in the field.
Automatic testing and verifications to ensure computation reliability.
Legal monitoring ensured by a dedicated team.
Management of all hosting facilities directly by Amazon Web Services, according to ISO 27001.
All transmissions between client and server and to external systems are performed through end-to-end HTTPS encryption.
PayFit's network splits into subnetworks, each handling a specific function, both for performance and security enhancement.
Separation of testing and production environments.
Isolation of PayFit network from the Internet, with the exception of a single entry point (proxy). Each point inside the network follows strict firewall rules.
Protection of access to PayFit systems through AWS and Kubernetes rights management.
Access to data, by authorised staff members, is only allowed through a VPN protected by 2FA authentication.
Monitoring and log of data transmission from IT systems that store or process personal data.
Synchronisation of all servers through an AWS NTP server.
Deployment of audit logs to trace authentication and monitor logical system access, as well as data access and modifications.
Systems technical events, such as errors, are monitored and logged separately.
Access to logs through a specific name space, a VPN with mandatory 2FA authentication and password protection.
Logs data is automatically replicated on three nodes in three different areas in France (AWS servers, certified ISO 27001). All data is handled on servers with an automatic failover system.
Retention of audit logs is set to one year.
Replication of all data continuously on two nodes for our databases and on three nodes for our AWS S3 storage. Each node is hosted in a specific data centre, separate from others. All data is handled on servers with automatic failover system.
Backups every hour and full recovery process verified on a daily basis.
Transmission of backups through end-to-end HTTPS encryption.
Backups are replicated three times. All accesses are protected through AWS and Kubernetes rights management.
PayFit has implemented a formal procedure for security events and has trained all staff members on it.
When security events are detected, they are escalated to our emergency alias. Subsequently, teams are automatically notified and gathered to rapidly address the incident.
The analysis is reviewed in person, distributed across the company and includes action items that will make the detection and prevention of a similar event easier in the future.
Security events must be systematically reviewed for closing by the engineering, security, legal and communication departments. Any other affected teams are also consulted.
Use of technology such as Sentry and AWS Cloudtrail to provide an audit trail over its infrastructure and the PayFit application. Auditing allows to perform ad-hoc security analysis, track changes made to the PayFit setup and audit access to every network layer.
Run of a private bug bounty programme on HackerOne to identify and mitigate security threats. Access to this programme is by invitation only.
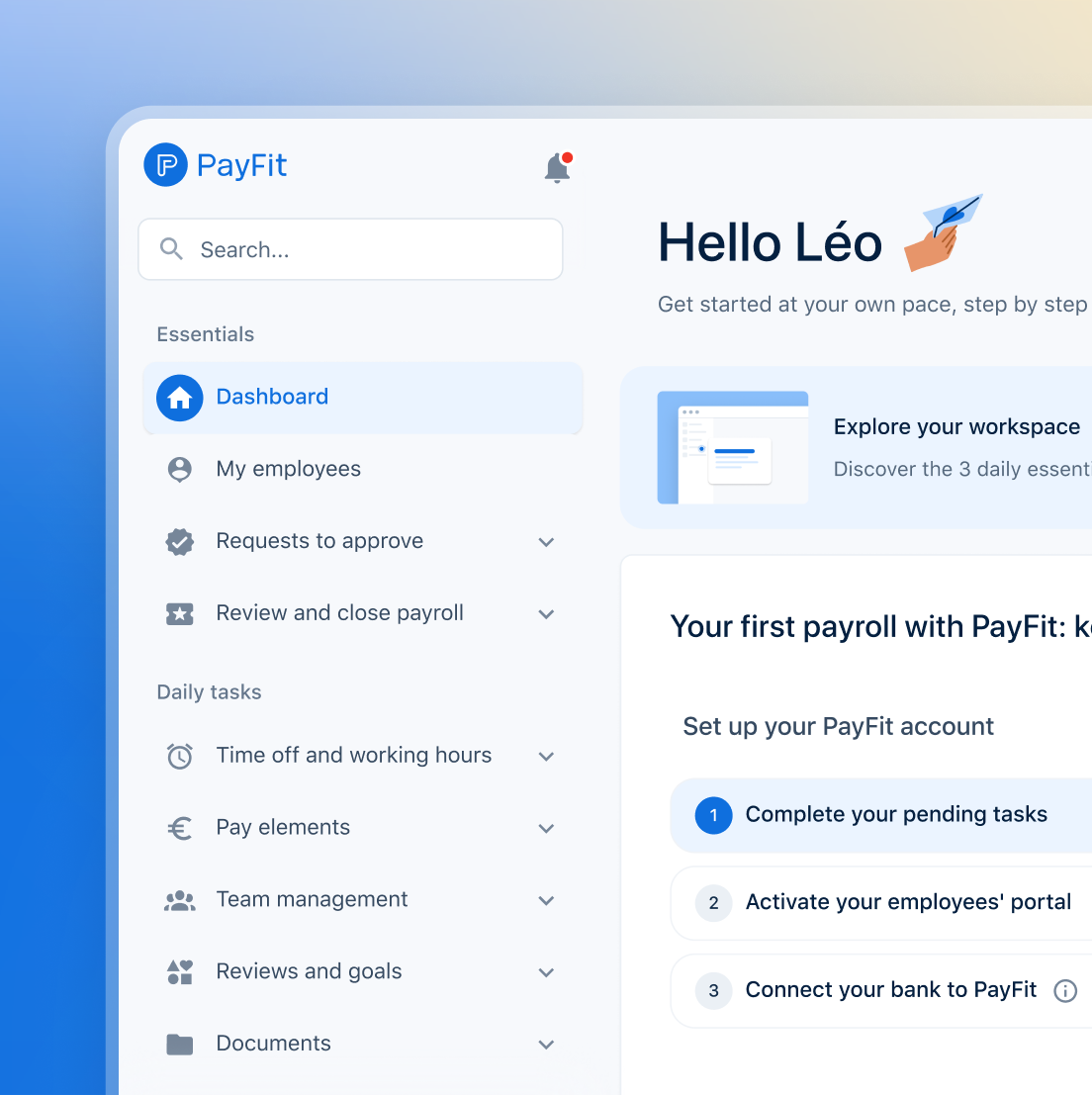
See what's new in PayFit
New features to save you time and give you back control. Watch now to see what's possible